If that’s the case then I am still seeing some people that should not be around. It now seems like eons ago that war nearly erupted between the US and Iran yet it was in January. Since then, we have experienced one of the most destructive wildfires in Australia, there was a locust invasion in Africa, various natural disasters have hit different parts of the world and yet, all that pales when compared to the novel Coronavirus. At the time of writing this, there have been 7.6 million reported cases of COVID-19 infection, and about half of a million people have succumbed to the disease. But, in the face of this turmoil, there is a group of people who are thriving. Hackers. Here is a shocker. Since the world got hit by the pandemic, scammers have gotten away with $46.2 million from unsuspecting victims. They have achieved this through a combination of scams including phishing emails and texts, fake online shops, and phone calls. In this post, we are going to look at exactly how the scams are executed, some of the most popular ones to look out for, and how to ensure that you don’t become a victim. One method being used by the cyber-terrorists to infect victims with malware is creating fake sites that offer coronavirus statistics. People everywhere are curious to know how the pandemic is spreading across the globe. Which countries have been most affected, how many new cases of infection and death have been registered on a particular day, how many people have recovered? You will find a lot of websites with this information but not all of them can be trusted. For instance, cybersecurity expert Shai Alfasi discovered a fake website that has been designed to resemble a popular COVID-19 map website created by John Hopkins University. Once you open the fake map it activates a malware known as AZORult that records your personal information including browsing history, username, passwords, and can even be used to steal your crypto. Apart from stealing your data, AZORult can act as a gateway for other malware into your system. This is by far the most popular method used by cyberattackers to scam people. Probably because it allows them to target a large demographic. How this works is that the hackers send emails posing as a legitimate person or company to trick the receivers into clicking malware-infected links or downloading infected attachments. Here are some examples of phishing emails identified by various security solutions.
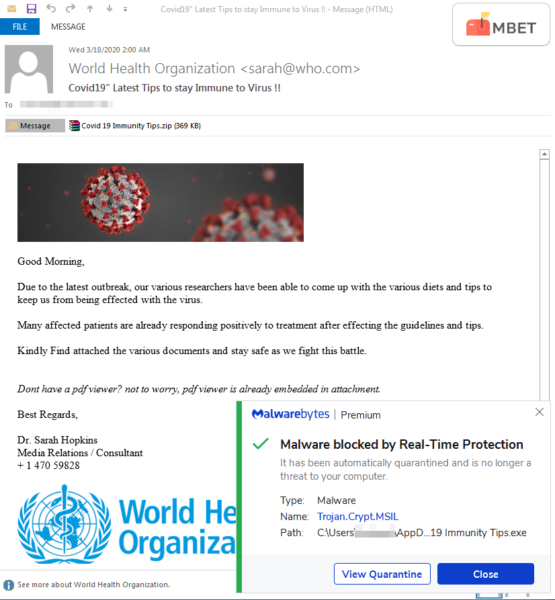
Phishing emails supposedly from WHO
WHO is the agency responsible for international health for the United Nations and so any information coming from them will immediately pass the credibility test. This makes them high targets for impostors. Quick question. If you opened your email today to find a message from WHO containing a home remedy for COVID-19, you would not think twice about downloading the guide, right? Well, the odds are that the email is not from WHO and what you are downloading is not a remedy but a malware that will open up your computer to other forms of cyberattacks. This was the case for one email flagged down by Malwarebytes Labs. The scammers posed as WHO professionals pushing an ebook that supposedly contains all research on the virus including its origin and how to effectively protect yourself and others. However, the ebook was embedded with malicious code for a downloader called GUloader which the hackers then used to secretly download an information-stealing trojan called Formbook into your system. The Formbook trojan can record your browsing history, collect data that is stored on your Windows clipboard, and also log your username and passwords as you enter them. In another similar instance also uncovered by the Malwarebytes Labs, hackers posed as WHO professionals offering tips on how to boost your immunity against the novel virus. They then integrated a keylogger software known as Agent Tesla into the pdf allowing them to record every keystroke you make on your keyboard. There was also another WHO email scam uncovered which promised COVID-19 immunity tips but was instead meant to inject the victim’s computer with the Netwire Remote Access Trojan (RAT). Once infected, the hackers would have full control over the user’s machine from wherever they are. This puts them in a position to steal all your personal information on the computer and also monitor your activities.
Phishing emails from company management to employees
There have been reported cases of employees receiving emails from management informing them of company policy changes resulting from the pandemic. The employees then proceed to download the attached files and you know how that ends. Just like all the other phishing email scams so far, there are different variations to this scam. The hackers may use a different story in their email but the goal is to get the receiver to click a malicious link or download a malware-infected attachment. Look, the list of all the coronavirus related scams is endless. A security researcher by the name @Sshell built a tool that actively scans the web for potentially malicious coronavirus domains being registered and you would be shocked at the number of potential scams being uploaded per minute. Also, according to Google, they identify and block over 100 million coronavirus related scams on Gmail every day. So what I highlighted is just a small fraction of the scams in circulation to give you perspective. And since you can’t rely on your email provider to filter out all the email scams, you need to be actively engaged to ensure you do not become a victim. It starts with you being able to recognize phishing scams by looking at them. Better yet, I recommend that you have a next-generation antivirus solution. It will take the pressure of identifying scams off you and is more effective in protecting you against threats. Most phishing emails have a standout aspect that sells them out. This is because cybercriminals are not as interested in the accuracy of the message as in sending it out to as many people as possible. It’s a numbers game or otherwise known as the spray and pray phishing technique. Here is how to know that the email you have received is not authentic.
The sender’s email address
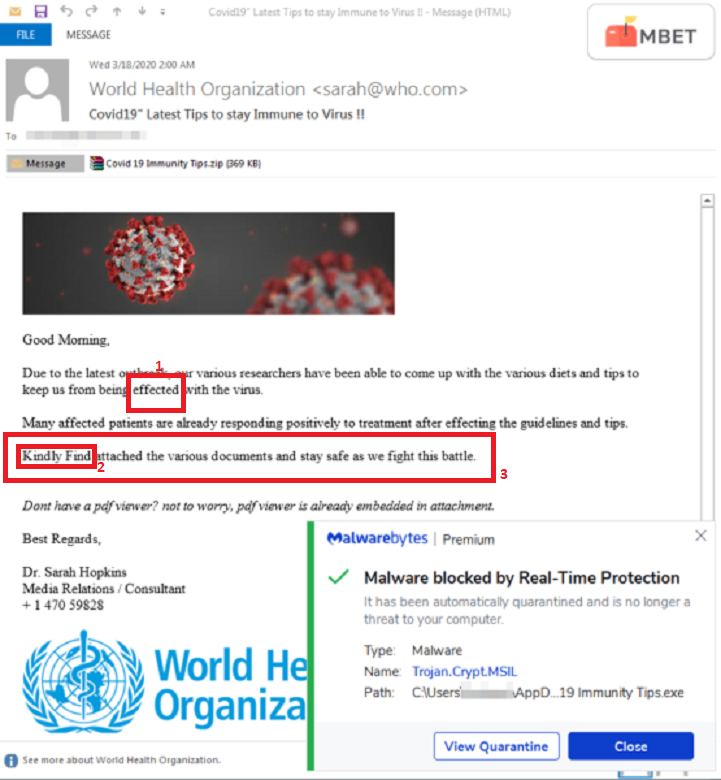
The general layout of a phishing email may look identical to that from a legitimate source but the sender’s address will most certainly not match that of the official site. A real email from an authentic source should have the company’s domain name at the end. For instance, an email coming from WHO would look as follows. xyz@who.int. Anything different from that like xyz@who.org or xyz@who.com is a scam. Taking this email, for example, you can tell that the email is fake since it’s from sarah@who.comIn the highlighted example the email seems to be coming from Sarah.
Watch out for grammatical and syntax error
This is the most common sell out when it comes to phishing emails. Sometimes the error is so glaring that you will want to laugh. Taking the email from Sarah above as an example, I can already spot three errors. The first is that she uses “effected” instead of “infected” when talking about the virus. The second is that she uses an uppercase letter in the wrong place. Finally, the last sentence in the email has a syntax error. The correct phrasing would be “Kindly find the various attached documents and stay safe”. I would also say the word various has been overused in the email. You need to understand that these organizations pay top dollar to access the most proficient email copywriters.
Take a closer look at the attached links
Before clicking on a link try hovering the mouse above it. This will display the whole link and you can then determine if it’s the actual site that you are supposed to visit.
Are they requesting for personal information
Legitimate entities will never ask for your personal information such as your password, credit card information, or social security numbers.
Generic salutations
If an organization is sending you an email then it means they already have your information and will, therefore, address the email to your real names. Scammers on the other hand will address the email to generic names such as sir/madam or completely forego the salutation like the email from Sarah.
Email demanding urgent action
Cybercriminals know that they have a better chance of scamming you if you are not thinking rationally. So, they will try and use threats to scare you into quick action. This way you don’t have enough time to question email authenticity. But like I said, sometimes it’s possible to miss the obvious signs in a phishing email. It’s also possible that the scammers are on an advanced level and are thus able to come up with a flawless fake email. That is where the antivirus comes in. Unfortunately, most of the traditional solutions will not be effective in stopping coronavirus related scams. This is because they rely on signatures that are already in their database to block threats. Since most of the corona scams are new they won’t be available on their database and will, therefore, be able to pass through the antivirus. What you need is a new-generation solution that uses behavioral analysis to detect suspicious activity. As usual, I will make things easy for you by recommending the best solution for the job (GET Malwarebytes) Malware is like antivirus but smart. That is a direct quote from their website. The security solution uses a combination of techniques such as anomaly detection, behavior matching, and application hardening to ensure that users are safe from all types of malware including the undiscovered ones. It also guarantees protection against all attack vectors that can be used by hackers. It blocks infected websites, flags down malicious links, blocks installation of malware-laden apps, and also blocks phone call scams. In case you have already fallen victim to the scam and your computer is infected, Malwarebytes promises to flawlessly clean up your system so that there are no traces of the malware. This has been corroborated by AV-Test, an organization that tests and rates security solutions. Malwarebytes is available for use both in a personal or business environment and the price differs based on the number of devices you want to protect.
Fake online shops and services
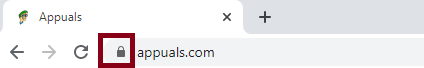
How this scam works is that sellers use false images to advertise their products or use false descriptions. The buyer, therefore, ends up getting completely different products than they ordered. And that is when they are being generous. Sometimes you will not receive anything at all. Sadly, there is nothing you can do because by the time you realize that you have been scammed the seller is already gone. Hackers can also use fake shopping sites to try and steal your financial information. To avoid getting caught in this scam, don’t purchase from sellers that you don’t know. Also, check the reviews left by other buyers. And lastly, check to see that the sites you use have a padlock icon on the address bar. This means that all data sent through the site is encrypted and cannot be intercepted by hackers looking to steal your usernames and passwords.
Fake fundraising schemes
Even as we grapple with all the negatives resulting from the pandemic, one thing that can give us hope is the number of selfless acts that we are seeing all over the world. People are foregoing full month salaries to help those affected. But you can always trust scummy individuals to ruin a good thing. There have been reported cases of scammers posing as charities raising money to help those affected by the pandemic only for that money to end up in personal accounts. In a related scam, hackers request that victims provide their personal information to facilitate the disbursement of donation money and then use this information to access and drain the victim’s financial account.
Stimulus check email scams
This scam alone has cost US citizens about $13.4 since the $1200 stimulus check initiative was launched. The scammers use email, text, or phone and execute the attack in two main ways. The first is that they impersonate the IRS and request that you send them your details to assist them to process your check. You already know what happens when the hackers have your personal information. The other technique being used is that the scammers mail you a fake check with a higher amount than the stipulated $1200 and then request that you refund them the excess.
Test the level of germs in personal homes
This is a new type of scam and is quite scary because it’s not happening online. The scammers trick their way into your house and a failure to cooperate could result in physical harm. How it works is that the criminals pose as a health agency that tests your home to rule out contamination with the coronavirus. There is no such initiative being conducted and so if you receive this type of request immediately shut it down. As with most online scams, the best measure that can be taken is to educate the mass about the existence of the scams. This is the whole purpose of this post. The best you can do is share this information with your friends and family. Also, various bodies such as the Federal Trade Commission (FTC) have initiated awareness campaigns to ensure that people know how to protect themselves. Interpol has also stepped in and is carrying out investigations in a bid to arrest the scammers.
Change all your passwords using an uncompromised device. There is a chance that the hackers are still monitoring your activities on the compromised device. Remember to use strong passwords and don’t use the same password for multiple accounts.Notify your bank and credit card provider. Once they know your account has been compromised they can start monitoring it for suspicious activity. Also, check previous transactions to confirm that the hackers have not already accessed your account.Report the incidence to the local body in charge of phishing scams.
These are unprecedented times we are living in and it’s easy to get caught up in the misinformation. I also understand the fear that comes with the novel coronavirus and that is exactly what the scammers are counting on. But remember this. Any information about a cure, vaccine, or any other type of remedy will be first communicated by WHO. For country-specific information about the virus check out the official websites of your countries health institution. If you are in the US you can rely on information coming from the Center for Disease Control (CDC) and if you are in the UK you can trust the National Health Service (NHS). My final advice. Maintain social distance, sanitize your hands regularly, and of course, watch out for those phishing emails. Stay safe.