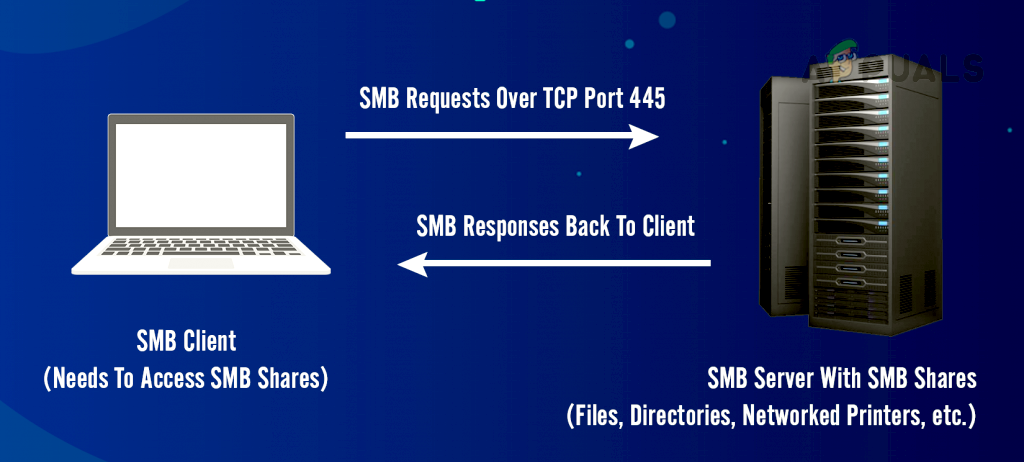
SMB Working Mechanism
In the simplest form, SMB client machines connect to an SMB server using the SMP port (port 445) to access SMB-based shares after successful SMB authentication. Once an SMB connection is established, file collaboration, printer sharing, or any other network-based operation can be performed.
History of SMB Protocol
SMB protocol was developed in the 1980s by a group at IBM. To meet evolving network requirements over the years, the SMB protocol has evolved through multiple variants, called versions or dialects. The protocol is still one of the most used protocols for resource sharing on LAN or in the workplace.
SMB Protocol Dialects or Versions
To be compatible with the ever-changing IT horizon, the SMB protocol has gone through many improvements from its original implementation of the SMB protocol. The most notable are the following:
SMBv1
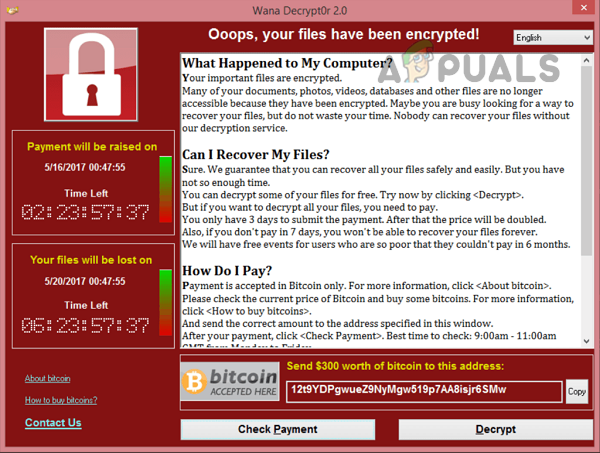
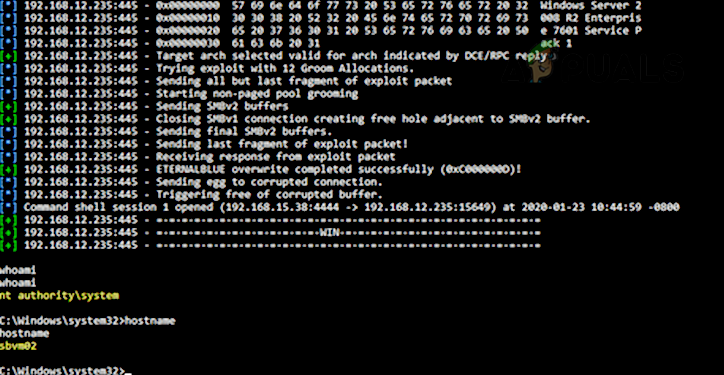
SMBv1 was developed back in the 1980s by IBM and renamed CIFS by Microsoft with added features in the 1990s. Although in its days, SMB 1 was a great success, it was not developed for today’s connected world (as with all the software applications developed in that era), after all, 30+ years of the information revolution have passed since then. Microsoft depreciated SMBv1 in 2013 and by default, it is no longer installed on Windows and Windows server editions. Due to its outdated technology, SMBv1 is highly insecure. It has many exploits/vulnerabilities and many of these allow remote control execution on the target machine. Although there were warnings from cyber security experts about the SMB 1 vulnerabilities, the infamous WannaCry ransomware attack made it very clear as the attack targeted vulnerabilities found in SMBv1. As a result of these vulnerabilities, it is recommended to disable SMB1. More details on the SMB1 vulnerabilities can be found on the Malwarebytes blog page. A user may himself check the SMB1 vulnerabilities (especially, EternalBlue) by using Metasploit.
SMBv2 and SMBv3
SMBv2 and SMBv3 offer the following enhancements to the SMB protocol (whereas SMB 1 lacks these capabilities): A natural question may come to some users’ minds if their systems have SMBv2 or 3, will it not cover the vulnerabilities of SMB 1 on a user’s machine? But the answer is no as these enhancements to SMB work differently and use a different mechanism. If SMBv1 is enabled on a machine that has SMBv2 and 3, then that may make the SMBv2 and 3 vulnerable as SMB 1 cannot control man in the middle (MiTM) attack. The attacker is just required to block SMBv2 and 3 on his side and only use SMB 1 to execute his malicious code on the target machine.
Effects of Disabling SMB 1
Unless essentially required (for machines running Windows XP or legacy applications using SMB 1), it is recommended by all the cyber security experts to disable SMBv1 on the system as well as on the organization level. If there is no SMBv1 application or device present in the network, then nothing will be affected but that cannot be the case in all scenarios. Every scenario to disable SMBv1 may differ but an I.T. administrator, may consider the following in disabling SMB 1:
Methods to Disable SMB 1
Many methods can be used to disable SMB1 and a user may use the method that best suits his scenario.
Disabled by Default
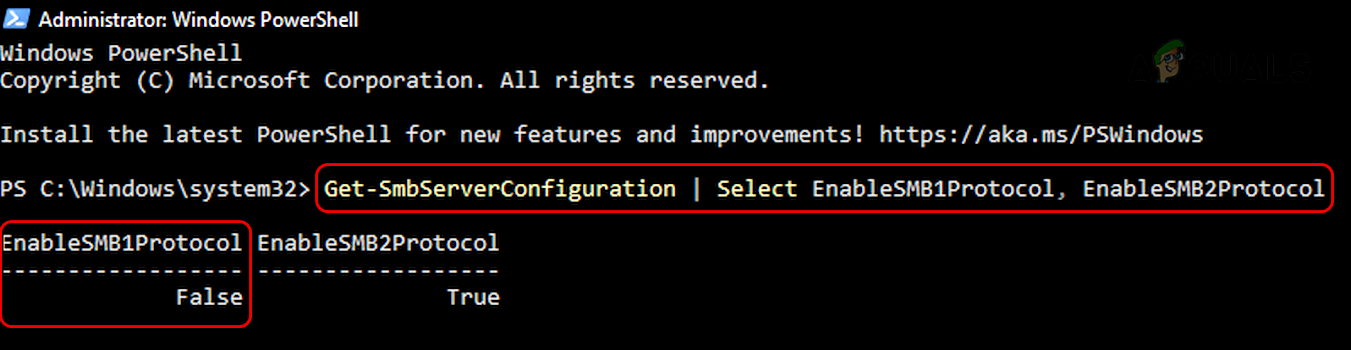
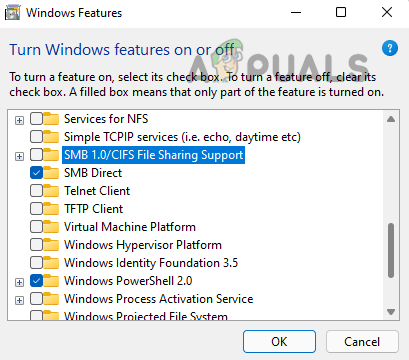
SMBv1 is disabled by default on Windows 10 Fall Creators Update and later versions. SMB 1 is disabled by default on Windows 11. For server editions, Windows Server version 1709 (RS3) and later have SMB1 disabled by default. To check the current status of SMB1: Keep in mind that Microsoft has included automatic removal of SMB 1 through Windows updates but if a user re-enables, then the protocol may not be disabled in the future and make the machine vulnerable.
Use Control Panel of Windows 10, 8, or 7
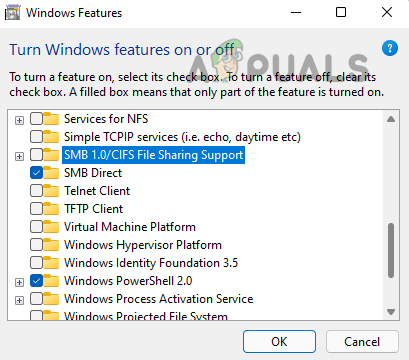
Use Optional Features Menu of Windows 11
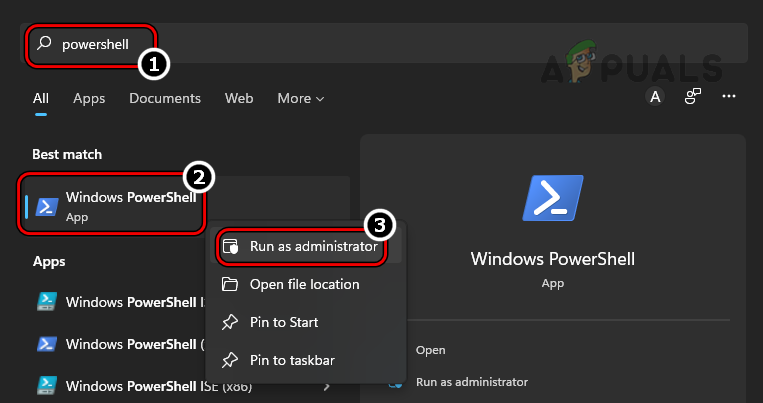
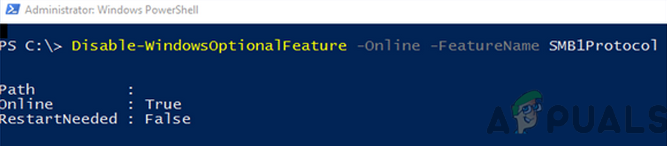
Use PowerShell
The above two methods may satisfy the requirements of maximum users, but on a server system, an admin may have to use PowerShell (although, steps may also work fine on a client machine).
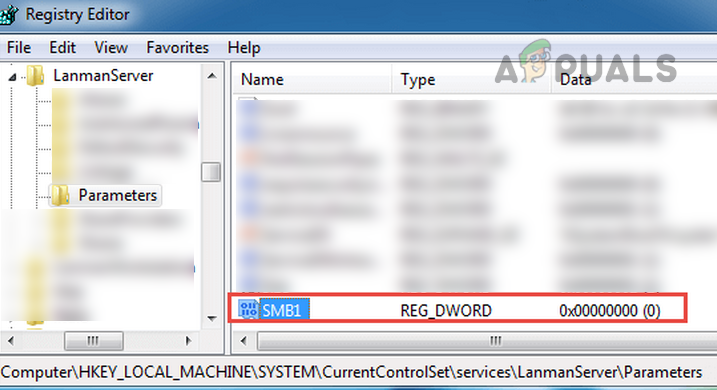
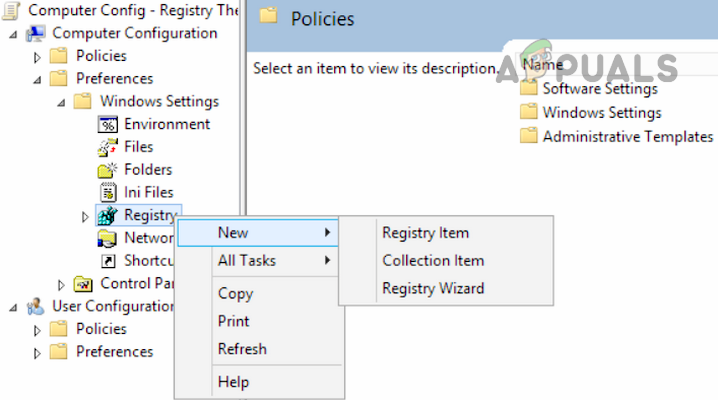
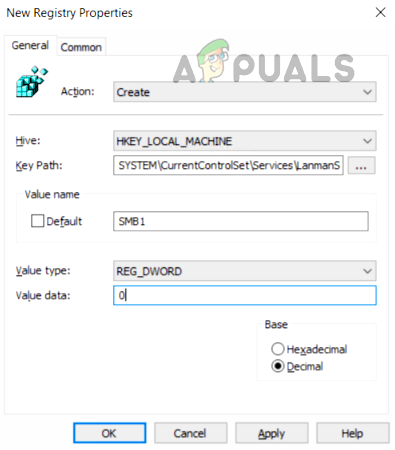
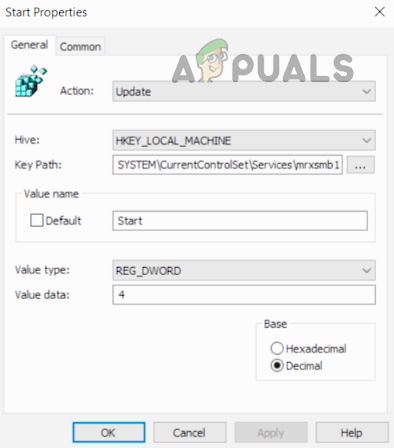
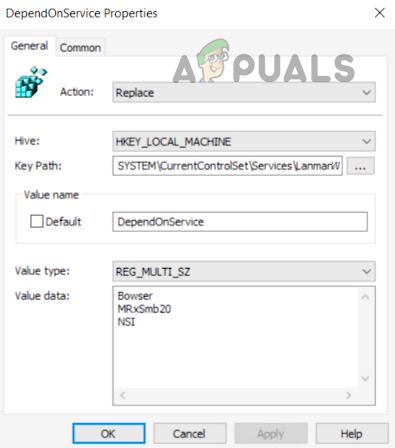
Use the System’s Registry Editor
An admin on a Server machine without PowerShell (like Windows Server 2003) may disable SMB 1 by using the registry editor although steps also work fine on a client machine. Warning: Proceed with extreme caution and at your own risk as editing the system’s registry is a proficient task and if not done properly, you may imperil your system, data, or network.
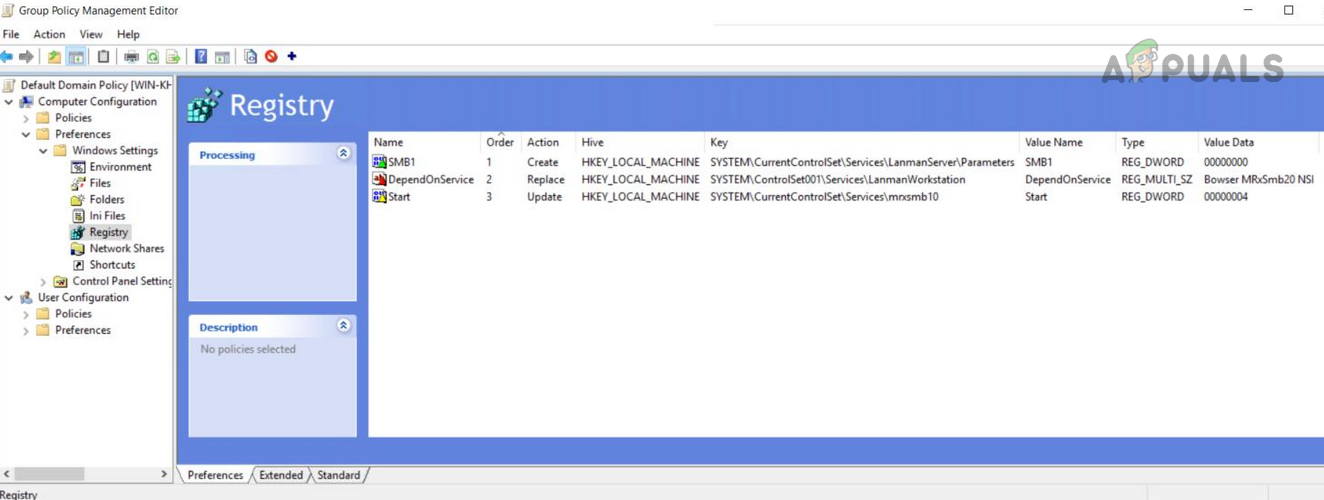
Use Group Policy Editor
Although the above steps work for individual machines but to disable SMB 1 on an organization level, an admin may use a Group Policy Editor.
Disable SMB 1 Server
Disable SMB1 Client
Disabling SMBv2 or 3
Some users, due to the threat level of SMB 1, may decide to disable SMBv2 or 3, which is unnecessary at this time. If a user disables SMBv2 or 3, he may lose:
Users Bind to Use SMB1
The following scenarios may force a user to use SMB 1:
Users with Windows XP or Windows Server MachinesUsers are required to use decrepit management software that requires system admins to browse via the network neighborhood.Users with old printers with ancient firmware to “scan to share.”
Only use SMB1 if there is no other way possible. If an application or device requires SMBv1, then it is best to find an alternative to that application or device (it may look costly for now but it will be beneficial in the long run, just ask a user or organization which suffered from WannaCry). So, that is it. If you have any queries or suggestions, do not forget to ping us in the comments.
1080p 144hz vs 1440p 75hz: Which Should you buy and why?USB 2.0 vs USB 3.0 vs USB 3.1: Which should you Have and Why?NVMe PCIe M.2 Vs. SATA - Which Should You Buy and Why?Which Sound Card Should You Buy and Why