What is ZAM.exe?
The genuine zam.exe file is the main executable belonging to Zemana AntiMalware – a highly appreciated malware removal kit. Of course, the zam.exe executable is in no way essential to your operating system since it’s only a 3rd party component with no relation with system services. It’s also possible that this executable was brought in by Zemana AntiLogger (even if you don’t have Zemana AntiMalware installed). UPDATE: As it turns out, this executable can also below to a few other applications: League of Legend, Watchdog Anti-Malware, Malware Killer, MalwareFox AntiMalware If the file belongs to Zemana AntiMalware, the purpose of this executable is to call upon and manage the services involved in the operation of scanning and removing malware, adware and another type of viruses (handled by Zemana AntiMalware). We’ve confirmed that this executable has the potential of using a lot of system resources, but only in the scenarios where Zemana Antimalware or Zemana AntiLogger is actively performing a scan.
Is ZAM.exe safe?
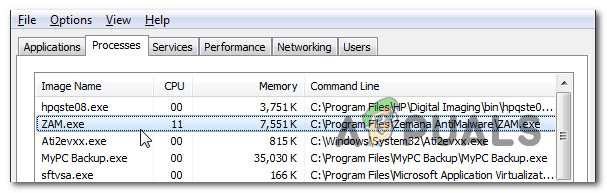
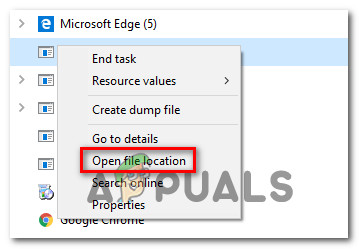
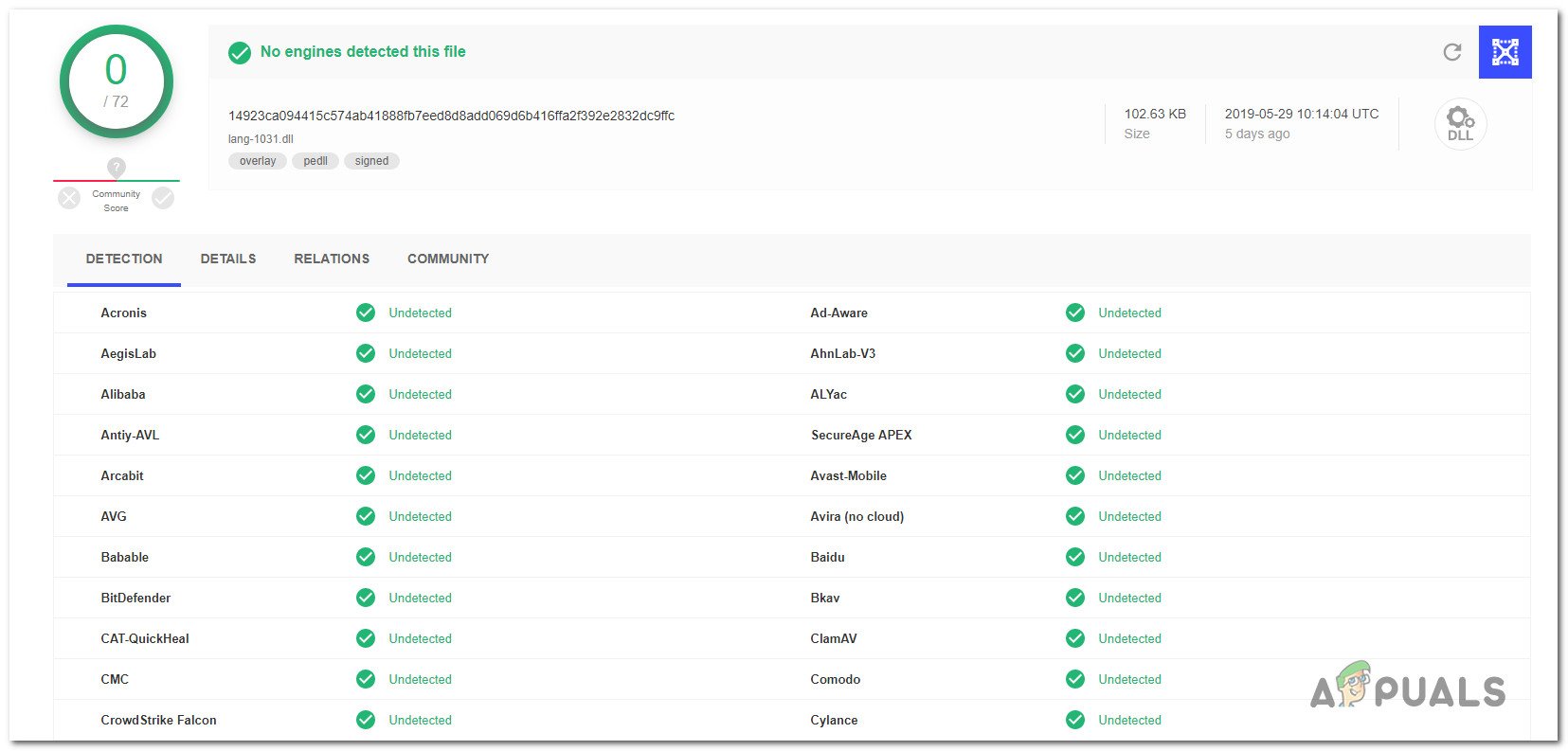
The genuine zam.exe executable is an integrated part of an antimalware component (if you have Zemana AntiMalware installed), so you have nothing to worry about when it comes to a security breach. But the key part here is figuring out if the executable you’re dealing with is indeed genuine. However, most successful modern malware products are designed with cloaking capabilities to avoid detection by security suites – This means that they are programmed to camouflage themselves as other trusted processes to avoid detection. With this in mind, we highly recommend that you take the time to investigate whether the executable you’re dealing with is genuine or not. The best place to start here is to see if you have installed any of the parent applications that might install zam.exe. Here’s a shortlist of software that has this executable (zam.exe): If none of these software are installed on your computer (and weren’t installed at some point), you can start considering the possibility of a rogue executable. Note: If you manage to identify the parent application and you confirm that the zam.exe executable is genuine, you can move directly to the Should I Remove Zam.exe? section. In case none of the parent applications are installed you should start investigating the location to see if the file is a remnant file from a previously installed application. To do this, press Ctrl + Shift + Esc to open up a Task Manager window. Inside Task Manager, select the Processes to tab from the horizontal menu, then scroll down to the list of Background processes and locate zam.exe. If the location is not located in a subfolder of Program Files or Program Files (x86) and you didn’t install it in a custom location, chances are you might be dealing with a security suite. If the location is a system path like C:\Windows or C:\Windows\System32, the chances of dealing with a malware executable are high. If the file is located in a suspicious location, it’s highly recommended that you upload the zam.exe file to a virus database to be analyzed. This process will allow you to determine if the file is indeed infected or not. Several different virus databases will allow you to do this, but we recommend VIrusTotal since it’s essentially an aggregator that encompasses most virus databases currently on the market. To upload the file into VirusTotal, simply access this link (here), upload the file and wait for the analysis to complete. If the analysis didn’t reveal any inconsistencies with the zam.exe file, you can safely move directly to the Should I remove Zam.exe? section. But in case the VirusTotal analysis is pointing towards a security infection, you should continue with the next section below for step-by-step instructions on resolving the virus infection.
Dealing with the security threat
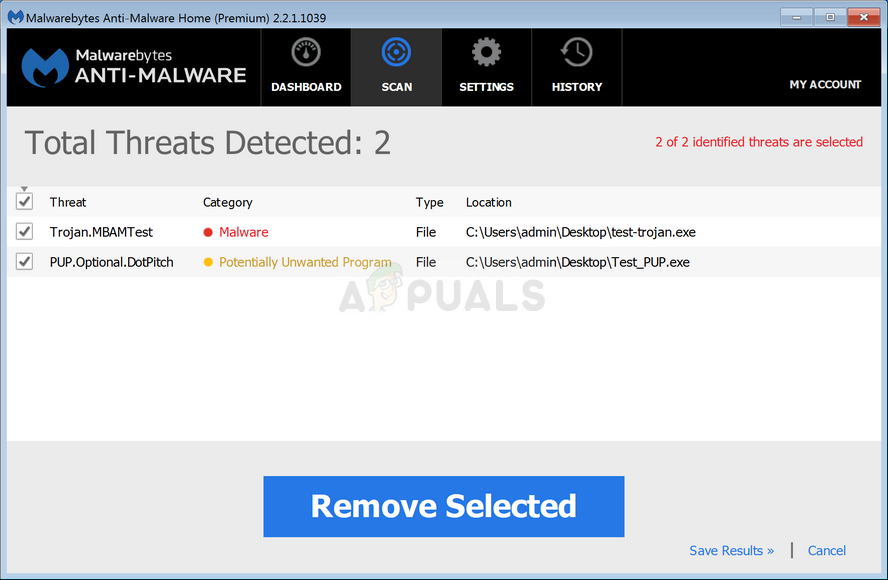
If the investigations above raised some suspicions regarding the legitimacy of zam.exe, you should perform a series of cleanup chores to remove every trace of malware infection (including zam.exe). Keep in mind that in the case of cloaking malware files, detecting and dealing with them is notoriously harder than with traditional malware files. Not all security suites are capable of detecting them and removing them properly. If you have a Premium security scanner subscription, you can initiate a scan with it. But if you don’t and you’re looking for an alternative that will not cost anything, you should install and use Malwarebytes. This security scanner is free and will allow you to remove the vast majority of malware with cloaking capabilities. The key point when using Malwarebytes is to deploy a Deep scan (not a standard scan). To ensure that you’re doing this right, you can follow this article here. If the scan managed to identify and remove the infected items, restart your computer and monitor the situation to see if zam.exe is still consuming a lot of system resources. In case the same issue is persisting, move down to the next method below for instructions on preventing the legitimate executable from limiting the system’s performance.
Should I remove ‘ZAM.exe’?
If the investigations above didn’t reveal any security issues, you can safely assume that the executable you’re dealing with is genuine. If the resource consumption of zam.exe is still high, you can safely remove it without fearing that it will affect any of your Windows components. But keep in mind that to remove Zam.exe effectively, you’ll need to uninstall the parent application, which is likely a security suite. However, uninstalling the security suite doesn’t mean that you’ll leave your system exposed to other malware infections – As soon as the 3rd party AV suite is removed, Windows will automatically re-activate the built-in security option (Windows Defender). In case you are determined to remove zam.exe along with its parent application, move down to the next method below.
How to Remove ‘ZAM.exe’?
If all the investigations you performed above have confirmed that the executable is not malicious but you still notice that zam.exe is consuming a lot of system resources, you can safely remove it along with the parent application to resolve the issue. Keep in mind that deleting just the main executable (zam.exe) without uninstalling the app will likely not resolve the issue. In this case, there’s a high chance that the main app installation will regenerate the executable even if you end up deleting it. Your best option here is to uninstall zam.exe along with the patent application to ensure that the excessive resource consumption will stop. Here’s a quick guide on doing this:
What is UNCServer.exe and Should I Remove It?What is Esu.exe and should I Remove It?What is Smartwebapp.exe and should I Remove It?What Is ss3svc64.exe and Should I Remove It?